Muhammad Awais
Member
- Messages
- 23
- Solutions
- 1
- Reaction score
- 1
- Points
- 3
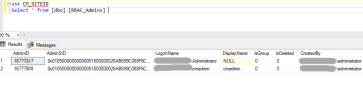
Security Scope "All instances of the objects that are related to the assigned security roles" greyed out for a user having a Full Administrator role.
I tried to turn it on because I was unable to turn on a feature in the Administration->Overview->Updates and Services->Features and then clicked on "Turn On" to find a message that would say "You do not have permission to enable features".

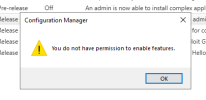
I tried to turn it on because I was unable to turn on a feature in the Administration->Overview->Updates and Services->Features and then clicked on "Turn On" to find a message that would say "You do not have permission to enable features".