RocheTechnology
New Member
- Messages
- 1
- Reaction score
- 0
- Points
- 0
Hello!
First I want to say what a fantastic resource your website is for us administrators! This community has saved me HOURS of time and taught me quite a bit, so thank you!
On to my question. We have rolled out Intune/Autopilot to our fleet of ~300 Windows 10 PC's. We have done so using Windows Hello and disabling Legacy authentication, essentially only allowing "modern" authentication, Windows Hello, to log into endpoints. So far, it's been working pretty well and with minimal issues.
However, we have a user who is leaving the company, and we'd like to prevent this user from being able to log into their endpoint once we deactivate the account. This seems like it would be very easy, but as it turns out, blocking the sign in and revoking the Azure AD license still allows the Windows Hello PIN/Fingerprint to log into the device. Doing some more digging in the Azure console, under User > Authentication Methods, there's an option to delete the Windows Hello entry here:
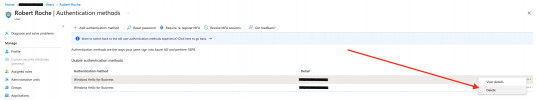
However, even after deleting that authentication method (and waiting up to 2 hours), I am still allowed into the device using fingerprint or PIN. Microsoft has fantastic documentation for deploying Windows Hello, but not much regarding removing it for an offboarding scenario. We can't immediately just perform a wipe because we need to keep the user's data/profile intact for a period of a few weeks after the offboarding date.
I've seen that there are some scripts that can be run on the endpoint to clear the database used for Windows Hello, but that sounds like more of a band-aid, one-off solution rather than an action performed in the Endpoint Manager console.
Is there a way where we can prevent the user from logging into the endpoint, as well as preserve the user's data?
Thank you for your time!
First I want to say what a fantastic resource your website is for us administrators! This community has saved me HOURS of time and taught me quite a bit, so thank you!
On to my question. We have rolled out Intune/Autopilot to our fleet of ~300 Windows 10 PC's. We have done so using Windows Hello and disabling Legacy authentication, essentially only allowing "modern" authentication, Windows Hello, to log into endpoints. So far, it's been working pretty well and with minimal issues.
However, we have a user who is leaving the company, and we'd like to prevent this user from being able to log into their endpoint once we deactivate the account. This seems like it would be very easy, but as it turns out, blocking the sign in and revoking the Azure AD license still allows the Windows Hello PIN/Fingerprint to log into the device. Doing some more digging in the Azure console, under User > Authentication Methods, there's an option to delete the Windows Hello entry here:

However, even after deleting that authentication method (and waiting up to 2 hours), I am still allowed into the device using fingerprint or PIN. Microsoft has fantastic documentation for deploying Windows Hello, but not much regarding removing it for an offboarding scenario. We can't immediately just perform a wipe because we need to keep the user's data/profile intact for a period of a few weeks after the offboarding date.
I've seen that there are some scripts that can be run on the endpoint to clear the database used for Windows Hello, but that sounds like more of a band-aid, one-off solution rather than an action performed in the Endpoint Manager console.
Is there a way where we can prevent the user from logging into the endpoint, as well as preserve the user's data?
Thank you for your time!
Last edited:
