jdwheaton
New Member
- Messages
- 2
- Solutions
- 1
- Reaction score
- 0
- Points
- 1
Hi everyone, we are deploying Defender in our environment to Windows servers (2016 and 2019). I'm able to successfully deploy Defender antivirus policies and can confirm this on the clients. However, in the SCCM console I'm getting mixed results as far as the information coming back from the clients. I have some that show up with "Enabled" in the "Endpoint Protection Enabled" column along with a current version of the definition files and "Succeeded" in the "Endpoint Protection Policy Application State" which is all to be expected. I'm also getting some clients that only have the "Succeeded" in the "Endpoint Protection Policy Application State" column and blank in the other two. Has anyone come across this?
For troubleshooting I have restarted the client, performed a repair on the SCCM client, kicked off the "Download Definition" on the collection as well. Thanks for any help or direction for further troubleshooting.
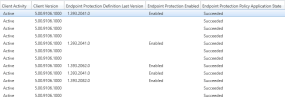
For troubleshooting I have restarted the client, performed a repair on the SCCM client, kicked off the "Download Definition" on the collection as well. Thanks for any help or direction for further troubleshooting.

